How can you protect internet exposed assets from exploit?
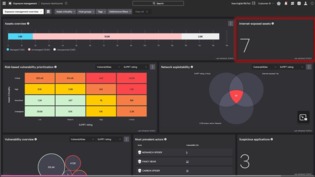
Lack of visibility into internet exposed assets amplifies the risk of cyber-attacks, data breaches, and compliance violations in your organization—thereby impacting business integrity.
How do you prevent such an occurrence? By automatically identifying internet exposed assets, you can dismantle risks before they’re exploited by an adversary.
Learn how CrowdStrike’s Internet Exposure Identification does so, in part by correlating exposed assets with vulnerability context to prioritize the most critical gaps, in this demo video.
