You've requested...
Bénéficiez de la puissance du Cloud AWS pour l'ensemble de votre SI
Download this next:
Enfrentando de frente as questões de desempenho dos microserviços
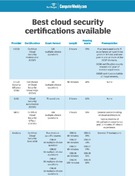
With the number of enterprise cloud deployments growing by the day, having someone well versed in cloud security on an IT team is integral to securing today's distributed environments. Many professionals seeking a career in cloud security will turn to certifications to advance their learning and prove their knowledge to potential employers. Here are some of the best cloud security certifications to consider in 2022.