HP Integrity NonStop NS1000 Server: Standards-Based Innovation at the Entry Level for Business-Critical Applications
By: Hewlett Packard Enterprise View more from Hewlett Packard Enterprise >>
Download this next:
GoSecure’s security suite in action
By: GoSecure
Type: Case Study
Nova Scotia Pension Services Corporation (NS Pension) was created as an independent, non-profit corporation, and currently services more than 74,000 active members.
But these services require NS Pension to handle a large volume of highly sensitive member data, putting them at increased risk for cyberattacks.
Download this case study to learn how GoSecure provides insights to help NS Pension improve its security posture.
These are also closely related to: "HP Integrity NonStop NS1000 Server: Standards-Based Innovation at the Entry Level for Business-Critical Applications"
-
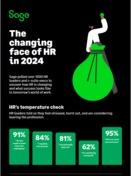
How HR is changing in 2024: What to expect
By: Sage
Type: Infographic
Sage polled over 1000 HR leaders and c-suite execs to uncover how HR is changing and what success looks like in tomorrow’s world of work.
Check out this infographic to get a sneak peek of what the HR role is shaping up to be in 2024.
-
Has HP taken a calculated risk in splitting the business?
By: TechTarget ComputerWeekly.com
Type: eGuide
This is a trend in the IT sector where multifaceted, publicly listed suppliers increase business lines over the years but are unable to gain full potential value from individual parts.
Dividing HP into two would also bring its PC business full circle having acquired Compaq for $21bn in a controversial deal in 2002.
Find more content like what you just read:
-
The Monsters in Your Software Supply Chain
By: ReversingLabs
Type: White Paper
Software supply chain attacks are up over 1000%. Are you prepared to confront the monsters that hackers are setting loose in your software supply chain? Download the new white paper to help arm yourself with knowledge and the tools to stay ahead of the modern software attack.
-
Security and efficiency with entry-level hardware security modules (HSMs)
By: Utimaco
Type: Product Overview
Security is often constrained by limited resources, but with entry level hardware security modules (HSMs), tailored to function seamlessly within these limitations, security doesn’t have to come at the expense of efficiency. Unlock Utimaco’s catalogue of offerings and find the HSM that’s right for your organization.
-
Web Browser Security Features Make Attacks Harder
By: TechTarget Security
Type: eGuide
This e-guide from SearchSecurity.com explores the features Microsoft Internet Explorer, Mozilla Firefox, and Google Chrome are developing that are making the job of the attacker much harder.
-
What does “continuous scanning” really mean?
By: Crytica Security, Inc.
Type: White Paper
While numerous cybersecurity vendors have applied the term “continuous scanning” freely to convey the speed at which their MDR, EDR, XDR product offerings operate, in reality, many of these product offerings fall short of deserving a “continuous” classification. Discover what it takes to truly achieve continuous scanning in this white paper.
-
6 retail transformations that wireless makes possible
By: Cradlepoint
Type: Product Overview
How can wireless networking transform retail? In 6 key ways. This overview outlines the retail transformations that LTE and 5G make possible – and how they can improve operations and customer experiences. Read on to access the insights.
-
New Flash Technology: Data Placement Automated Based on Hot Data
By: TechTarget Storage
Type: eGuide
NetApp recently launched the FAS2220, a new entry-level storage system, and Flash Pools, a caching method for RAID groups which combine solid-state drives and hard drives. Check out this expert tip guide to learn the details and the projected competitors of this product.
-
MicroScope - December 2017: Unlock the potential of DaaS
By: MicroScope
Type: Ezine
This month's MicroScope ezine looks at the issues around device as a service (DaaS), the outlook from HP and a report from the UK CompTIA conference.
-
Computer Weekly storage case studies
By: TechTarget ComputerWeekly.com
Type: Case Study
Antony Adshead takes a look at what made the winning entries stand out from the crowd in the Computer Weekly European User Awards.
-
MicroScope – May 2023: Vendors need to listen and learn
By: MicroScope
Type: Ezine
In this month's MicroScope ezine, we look at why it is vital that vendors listen to partners and act on the feedback. We also look at what's next for HP's advancing sustainability programme, Amplify Impact. Read the issue now.
-
Securing the perimeter-less network with increased visibility
By: Fortinet, Inc.
Type: Product Overview
With the death of the network perimeter, cybercriminals have proven that every asset is a potential entry point for an attack. FortiGate Next-Generation Firewalls
-
Microsoft Fabric for government agencies: Quick guide
By: Avanade
Type: White Paper
To harness the power of AI, government and public service agencies need a strong data foundation. Read this white paper to find out how you can establish such a foundation at your agency.
-
Best practices for ensuring security of all identities
By: SailPoint Technologies
Type: eBook
Compromised identities are an ever-present danger and are often found used by hackers as the entry point for calculated attacks. This book explores how strong identity security helps mitigate identity-related risk from hackers and human error, as well as how it can be used to streamline fortify governance and compliance. Download now to learn more.
-
Computer Weekly datacentre case studies
By: TechTarget ComputerWeekly.com
Type: Case Study
Jim Mortleman takes a look at what made the winning entries stand out from the crowd in the Computer Weekly European User Awards.
-
How to manage an endless stream of digital identities
By: SailPoint Technologies
Type: White Paper
The quantity of identities that most organizations are responsible for is so overdeveloped, that for many, manual identity management is no longer possible.SailPoint has developed their own AI-driven identity security solution, designed to affectively mitigate the risks presented by unmanaged identities. Download now to learn more.
-
Elevate your sales pipeline with AI-driven insights
By: Exponentia.ai and Databricks
Type: Video
In this video, you’ll learn about an AI-driven sales intelligence platform designed to help you improve sales conversations, gain market insights, and eliminate data entry tasks. Tune in to learn how you can create a 360-degree view of customer interactions and your team’s performance to closely monitor KPIs and elevate your sales strategy.
-
Empower your workforce with augmented reality
By: TeamViewer
Type: Product Overview
In maintenance and inspection, technicians need both of their hands. With smart glasses, a technician can see all relevant information, checklists, and diagrams directly in front of his or her eyes. Read on to learn how you can you digitize your knowledge with augmented reality instructions to enable faster processes and better results.
-
CW Benelux February 2018
By: TechTarget ComputerWeekly.com
Type: Ezine
In this issue, read about how and why one public sector IT professional in the Netherlands, Victor Gevers, took a whole year out to hack ethically and, in the process, unearthed about 1,000 vulnerabilities.
-
4 types of server hardware and their pros and cons
By: TechTarget ComputerWeekly.com
Type: Infographic
Servers host applications, manage files and perform analytics. Any organization can benefit from the power and versatility that servers provide, but it can be difficult to know which types of server hardware to choose. In this infographic, we take a look into the major types of servers, their advantages and disadvantages.
-
Optimize performance, cost, and control across your hybrid cloud
By: Hewlett Packard Enterprise
Type: White Paper
While organizations need hybrid and multi-cloud deployments, many are still plagued by the question: How do you optimally allocate workloads between clouds and on-premises locations in order to optimize performance? Download this white paper to see how HP answers this question.
-
Already Have AP Automation? Think Again.
By: Documation Software Ltd
Type: White Paper
When you think of accounts payable automation, many organizations think they have it all figured out with their solution that is a few years old or more. However, with the rapid advancements in technology over the past few years, AP automation looks much different now than the days of fax machines and OCR software. Read on to learn more about it.
-
4 ways to reap virtualization benefits through budgeting
By: TechTarget Data Center
Type: eGuide
When it comes to virtualization, budget planning is the key to success for any organization. This e-guide reviews why no matter what kind of cost saving benefits virtualization promises, having an established budget is essential to help with new purchases, ongoing support and software licensing costs.
-
3 ways to accelerate productivity and innovation in the enterprise
By: ServiceNow
Type: White Paper
This ServiceNow white paper details 3 ways to accelerate enterprise productivity and innovation, including connecting processes, hyperautomating tasks, and orchestrating workflows. Read the full paper to learn how you can drive faster decisions, save time and money, and empower employees.
-
Identity security with the power of AI
By: SailPoint Technologies
Type: eBook
Today’s enterprises are each responsible for up to millions of identities. But the scope of identity management means it is no longer feasible for humans to manage and secure these identities. SailPoint Identity Security for Cloud is designed to overcome these challenges by using AI to keep track of identities. Read on to learn more.
-
60-pg e-book: Global threat trends report
By: Elastic
Type: Research Content
The last year has seen a massive range of threats from both new and established criminals - delivering an onslaught of attacks designed to leave security teams unaware and overwhelmed. Browse this 60-page research report to discover threat phenomena, trends, and expert recommendations designed to help your organization prepare for the future.
-
Gen AI: Top concerns, new insights & business consequences
By: Connection
Type: eGuide
AI tools come with many perceived benefits but concerns regarding data privacy and trustworthiness remain relevant. Download this 52-page custom TechTarget eGuide to explore both sides in greater detail and learn how different industries are applying generative AI to find strategic business success.
-
Case study: Emissions firm scales fast with IoT
By: Particle
Type: Case Study
Qube is a company that provides an emissions monitoring solution to oil and gas companies. The company faced scaling issues with its hardware and partnered with Particle to gain integrated cellular connectivity and OTA updates. Read the details in this case study.
-
E-Brief: Capacity Planning for Virtualized Infrastructure
By: TechTarget Data Center
Type: EBRIEF
Explore current trends and tools for capacity planning in this e-brief. Discover how you can maximize server space and overcome top challenges of capacity planning to increase server utilization and ROI these tips from virtualization pro David Davis.
-
Malware Attacks Demand a New Malware Defense Approach
By: TechTarget Security
Type: eGuide
Customized, targeted malware attacks require new defense measures beyond those currently in place. This e-guide from SearchSecurity.com offers advice on protecting your organization from these new threats. View now to learn more!
-
The state of the threat landscape
By: CrowdStrike
Type: Research Content
The advent of AI as a tool has lowered the barrier of entry for hackers, only adding fuel to the fire that is the rapidly expanding threat landscape. With this 2024 Global Threat Report, CrowdStrike’s elite Counter Adversary Operations team delivers actionable intelligence you can use to stay ahead of today’s threats. Read on to learn more.
-
3 simple steps for stopping ransomware attacks
By: Illumio
Type: White Paper
Ransomware exploits the trends that have come to define modern business, taking advantage of the many entry points within today’s digital environments. This white paper aims to help you overcome the threat of ransomware, providing 3 simple steps you can use to increase your security capabilities. Download the white paper now to learn more.
-
Understanding Today's Threat Actors
By: Fortinet, Inc.
Type: White Paper
While attackers’ increasingly sophisticated activities should sound alarm bells, that same sophistication gives organizations ample opportunity to stop these attacks before a threat actor can achieve their objectives. For more insights on attacker activities and recommendations for effectively protecting your organization, download the full report.
-
The Secret Weapon in the Fight Against Sprawl
By: TechTarget IT Operations
Type: eBook
In this 3-part guide, learn about the ongoing battle against virtual machine sprawl and measures that can be taken when you've found an abandoned VM in your system. Access now to also learn about available automation tools that can be used to streamline virtualization duties and address VM provisioning and deprovisioning.
-
Compliance and Cloud Security eBook
By: TechTarget Security
Type: eBook
SearchSecurity.com presents a comprehensive guide to compliance and cloud security. Our experts cover all the angles in order to help clarify security and compliance issues associated with cloud computing.
-
A roadmap to take your IT services above & beyond
By: Schneider Electric
Type: Product Overview
The ongoing digital evolution, tied with increasing customer demands, has put pressure on businesses to provide excellent IT services. Discover how the mySchneider IT Partner Program program can diversify and strengthen your unique business model with a wide range of business-driving tools, enablers, and resources in this e-book.
-
How the New England Patriots Achieved HR Victory Through Paycom
By: Paycom
Type: Case Study
The New England Patriots deployed Paycom's HR system to manage 5K employees across states. Paycom's mobile-friendly tech improved data integrity & employee engagement, but that’s not all. In this case study, discover how Paycom is one of the Patriot’s MVPs.
-
How open source is spurring digital transformation
By: TechTarget ComputerWeekly.com
Type: eGuide
From Linux to Kubernetes, open source has been key to efforts by organisations across APAC to transform digitally. In this e-guide, read how Malaysia's AmBank is using open source to engineer its software from the ground-up, ANZ Bank's move to Red Hat OpenShift, and what suppliers are doing to support deployments of containerised applications.
-
Data Center Servers and Storage E-Book Chapter 4: Reallocating Unused Server and Storage Hardware
By: TechTarget Data Center
Type: eBook
With a bit of planning, a specific tiering-out of your system priorities and a dash of virtualization, you can breathe new life into your old servers -- even as you bring in replacements with all of their powerful new capabilities. Read this e-book to learn more.
-
IT in Europe: Taking control of smartphones: Are MDMs up to the task?
By: TechTarget Security
Type: Ezine
In this Special European edition of Information Security magazine, gain key insight into the increasing risks of mobile devices and the strategies and tools needed to mitigate them. View now to also explore VDI security, cybersecurity threats, IT consumerization deluge, and much more.
-
Healthcare: Choosing the right technology partner
By: InterSystems
Type: Blog
MedTech companies are advancing with digital health solutions. Selecting the right tech and partner is crucial for interoperability, security, and cloud services. Choose a partner with healthcare experience and a solid track record to speed up market entry. Read the full article to learn how to overcome common challenges and drive innovation.
-
How AI at the edge is sparking the adoption of edge computing
By: Red Hat and Intel
Type: White Paper
Edge computing brings compute power near data sources, enabling real-time AI inference, operations, model refinement, and data engineering. However, edge AI's growth faces hurdles like fragmented ecosystems, legacy systems, hardware requirements, and market entry challenges. Read this report to learn how to overcome these challenges.
-
How to Plan for Tomorrow’s SOC, Today
By: Palo Alto Networks
Type: White Paper
This playbook outlines 7 best practices that will advance your SOC transformation efforts and allow your organization to start its SOC modernization journey. Read on to get started.
-
The case for automating hybrid cloud management platforms
By: Splunk
Type: eGuide
Hybrid cloud has been garnering a lot of attention lately. However, like any burgeoning technology, it still has several significant challenges. Dive into the challenges facing hybrid cloud and how automating cloud management can help.
-
Serving up server hardware
By: TechTarget ComputerWeekly.com
Type: eGuide
In this e-guide, find out why some companies are still hanging on to older hardware, the pros and cons of different types of server hardware, and what one Chinese tech giant is doing in the microprocessor space.
-
A Computer Weekly Buyer's Guide to Server Operating Systems
By: TechTarget ComputerWeekly.com
Type: eBook
In this 12-page buyer's guide, Computer Weekly looks at Microsoft's latest Windows release, the state of play in the battlebetween Linux and Unix, and the future of the server operating system.
-
E-Book: Virtualizing Your Infrastructure - Selecting Server Hardware for Virtualization
By: TechTarget Data Center
Type: eBook
Choosing the right server hardware to maximize virtualization benefits is an important investment. To gain the high consolidation ratios you're after, you need powerful-enough hardware to support your workloads and applications. In this expert ebook, explore the hardware consideration to keep in mind as you virtualize.
-
Serverless computing: What enterprises need to know
By: TechTarget ComputerWeekly.com
Type: eGuide
As the use of public cloud services has gathered steam within enterprises, so too has interest among IT leaders about embracing the principles of serverless computing. In this e-guide we take a closer look at the benefits and pitfalls of serverless, while shining a light on the ways that enterprises across the globe are putting it to use.
-
Essential Guide: Application Performance Management
By: TechTarget ComputerWeekly.com
Type: Essential Guide
This guide to managing application performance covers transaction speeds, networking, workflow and tools for performance detection and diagnosis.